The Web3 landscape is exploding! Daily active wallets hit a staggering 7.7 million in Q1 2024, a 77% increase, but with this growth comes a crucial challenge: security. Web3 projects lost an estimated $700 million in 2024 alone according to SolidityScan Hackhub.
Smart contracts, the backbone of dApps, are vulnerable. Even the best code can harbor risks. Traditionally, audits were expensive and slow, leaving developers with unaddressed security concerns.
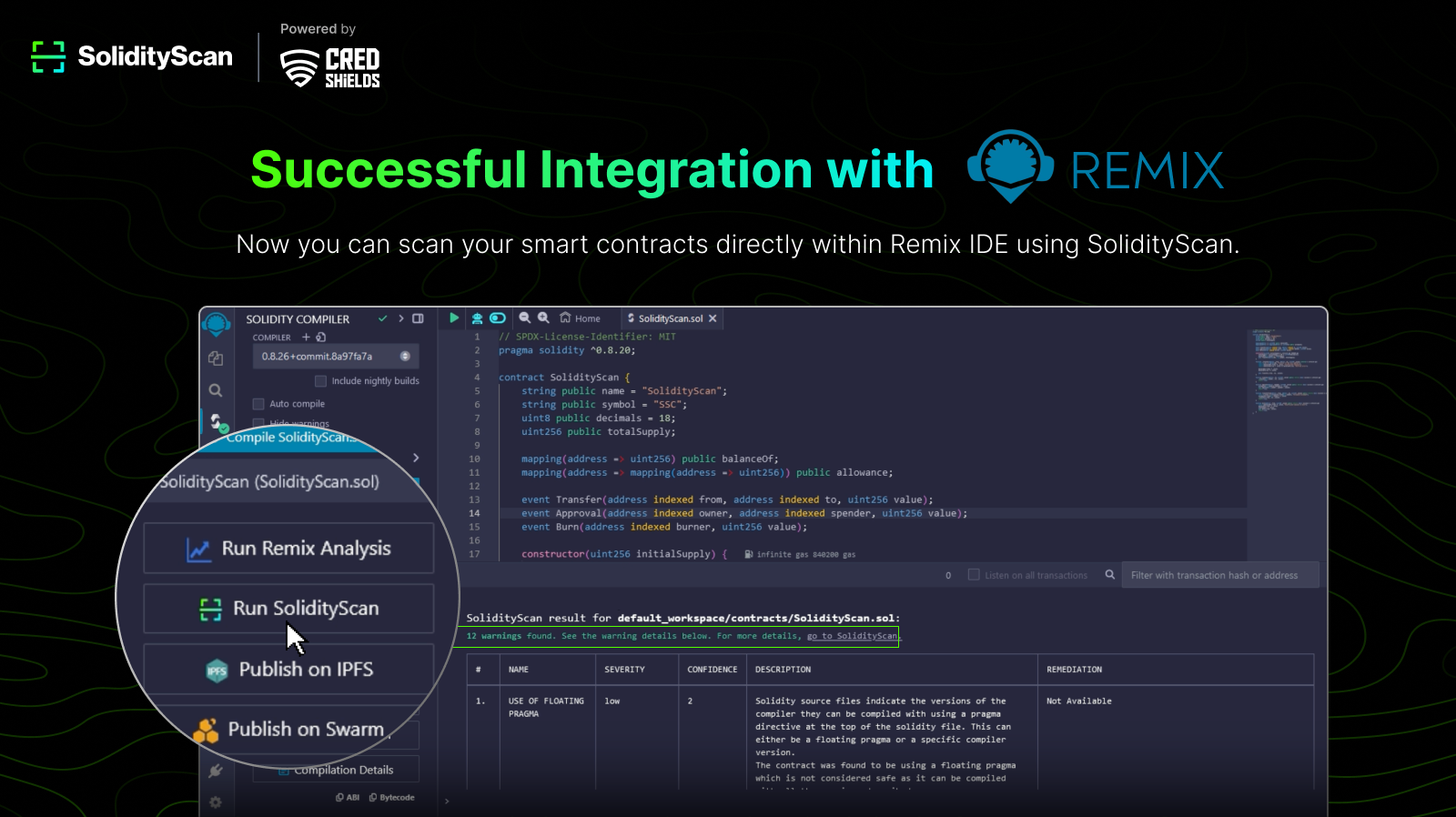
SolidityScan is here to help! Introducing our SolidityScan Remix Integration, bringing on-demand smart contract security analysis directly into your development workflow. This powerful integration works seamlessly with Remix IDE, your familiar coding environment. It leverages SolidityScan’s engine for real-time security insights, empowering you to build secure dApps with confidence.
This guide will walk you through using Remix IDE and SolidityScan to identify and address vulnerabilities in your smart contract code.
1. Setting Up Your Development Environment:
- Remix IDE: Remix is a popular online integrated development environment (IDE) specifically designed for working with Solidity smart contracts. No local installation is required – simply access it through a web browser at https://remix.ethereum.org/.
- SolidityScan Integration: Remix already integrates with SolidityScan, a powerful tool for automated smart contract security analysis. This eliminates the need for manual setup.
2. Importing Your Smart Contract:
There are two ways to import your smart contract code:
- Create a New File: If you’re starting from scratch, create a new Solidity file within Remix by clicking the “+” icon in the file explorer pane. Paste your code into the editor.
- Upload an Existing File: If you have an existing contract file saved on your computer, navigate to your file explorer and select the file for upload. Remix will import the code into its editor.
3. Compiling Your Code:
- Before running the security scan, it’s important to ensure your code is syntactically correct and compiles successfully. In Remix, locate the “Solidity compiler” section on the left-hand side of the interface. Click the “Compile” button to initiate the compilation process. If any errors are found, you’ll see them displayed in the “Compiler Errors” panel. Address these errors before proceeding.
4. Running SolidityScan:
- Once your code compiles successfully, a new option named “Run SolidityScan” will appear next to the “Compile” button. Click on “Run SolidityScan” and then confirm your action by clicking “Continue.” This will initiate the vulnerability analysis process.
5. Analyzing the Scan Results:
SolidityScan will analyze your code and present a comprehensive report. This report categorizes any vulnerabilities found, including:
- Vulnerability Name: A clear identification of the specific security weakness detected.
- Severity: Indicates the potential impact of the vulnerability, ranging from critical (high risk) to low (minimal risk).
- Confidence Level: Represents the likelihood that the identified issue is a genuine vulnerability.
- Description: Provides a detailed explanation of the vulnerability and how it could be exploited.
- Remediation: Offers guidance on how to fix the vulnerability and strengthen your smart contract’s security.
By carefully reviewing this report, you can gain valuable insights into potential security flaws in your code.
6. Learning More :
- The report may also include a link to the SolidityScan website. Here, you can find more information about specific vulnerabilities, potential mitigation strategies, and best practices for writing secure smart contracts. You might need to create an account on the SolidityScan website to access additional resources.
By following these steps and addressing any identified vulnerabilities, you can enhance the security of your smart contracts and protect your dApp from potential exploits.
SolidityScan’s integration with Remix empowers developers to write secure smart contracts with confidence. By incorporating real-time vulnerability analysis directly into your development workflow, you can proactively identify and address security concerns, saving time, resources, and ultimately protecting your dApps and their users.